Difference between revisions of "Seattle GridGuide Host"
(Created page with "==Description== thumb|Gaeatronics. Powering Seattle... naturally. Gaeatronics is an A-rated corporation owned by the Salish tribe. It provides po...") Tag: visualeditor-wikitext |
Tag: visualeditor |
||
| (7 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
==Description== | ==Description== | ||
GridGuide is a city's traffic control system, managed by a central host that sends routing data to vehicle autopilots and can track or control them in the event of an emergency. Contrary to the snazzy name, GridGuide is not a corporation, but a service provided by a corporate contractor; Seattle's GridGuide service is provided by Mitsuhama Computer Technologies. Because devices slaved to this host are ubiquitous in the Seattle Metroplex and easily accessed by hand, it's not hard to hack in. As a result, GridGuide hosts typically operate under Equipment Management Transfer Protocol (EMTP), more commonly known as an "industry host." See the next section for more details. | |||
==Scaffolding== | ==Scaffolding== | ||
The icon | [[File:Mitsuhama logo.png|thumb|363x363px|Mitsuhama Computer Technologies: The Future is Mitsuhama.]] | ||
The GridGuide host icon looks like a wheel with the Mitsuhama diamond at its center. When approached, it plays a jingle and displays the GridGuide logo as the wheel spins. | |||
=== | ===Customer Service=== | ||
{| class="wikitable" | {| class="wikitable" | ||
|+ | |+catp://www.gridguide.ec/ | ||
!Type | !Type | ||
!Rating | !Rating | ||
| Line 16: | Line 16: | ||
!IC Tray | !IC Tray | ||
|- | |- | ||
| | |Destination | ||
|7 | |7 | ||
| | |6 | ||
|6 | |||
|10 | |10 | ||
|Patrol, Bloodhound, Tar Baby, Track, Killer, Shocker | |12 | ||
|Patrol, Bloodhound, Tar Baby, Track, Killer, Blaster, Shocker | |||
|} | |} | ||
Inside, users will find themselves in a | Inside, users will find themselves in a sleek, polished corporate reception area. Virtual customer service representatives are always ready to help Seattle's vehicle owners register their cars with GridGuide. There is also a live traffic report feed that can be accessed from here, with the option to download the GridGuide traffic app for updates on the go. Because this is a destination node, one mark is granted freely to anyone who approaches. Silent-running is disabled inside. | ||
====IC Behavior==== | ====IC Behavior==== | ||
Patrol and Bloodhound will be running at all times. | Patrol and Bloodhound will be running at all times, with others kept in reserve. In emergency response mode, the host will spawn the highest priority IC in its IC Tray (see table). As a destination host, it will spawn each IC type per attacking persona at the start of each combat turn, though IC will not interact with any persona other than the one to which they are assigned. | ||
IC will not attack unless a hacker succeeds in an Attack action or fails a Sleaze action. If a hacker does not fight the IC or attempt any further illegal activity, the host will not enter alert, and the IC will stand down. Continued attacks will cause the host to enter emergency response mode; for each attack after the first a host suffers in a combat turn, its Firewall increases by 1 for 2 combat turns. If a hacker's attacks persist longer than 1 combat turn or the host gains 2 marks on them, a spider will be alerted. | |||
Personas with only 1 mark are not subject to Patrol IC scanning. | |||
====Devices==== | ====Devices==== | ||
This host does not have any slaved devices. | |||
====Spiders==== | ====Spiders==== | ||
There are no spiders on active patrol in this host, but if a spider is alerted, one will appear within a combat turn or two. The first spiders called in will be new acquisitions, deckers brought into the corporation via one of the numerous subsidiaries MCT has purchased in recent years, and so they will lack the experience and firepower of a Zero-Zone veteran. However, if you continue to cause trouble for long enough, a more veteran decker may be called in from corporate security duty for a bit, and they will immediately escalate to lethal force, having no sympathy for you. | |||
=== | ===Traffic Control=== | ||
{| class="wikitable" | {| class="wikitable" | ||
|+ | |+emtp://internal.gridguide.ec/ | ||
!Type | !Type | ||
!Rating | !Rating | ||
| Line 46: | Line 50: | ||
!IC Tray | !IC Tray | ||
|- | |- | ||
| | |Industry | ||
|7 | |7 | ||
|9 | |||
|8 | |8 | ||
|7 | |7 | ||
|10 | |10 | ||
|Patrol, Blaster, Tar Baby, Track, Marker, | |Patrol, Bloodhound, Blaster, Tar Baby, Track, Marker, Sparky | ||
|} | |} | ||
There is an employees-only area that can be accessed through a door marked "TRAFFIC CONTROL." Users who enter are transported into a vast, digital facsimile of Seattle represented as a series of neon-colored wireframe vehicles, traffic devices, roads, and buildings against a black background. Personas are free to fly above the city at blistering speeds, zipping from location to location in an instant. Solid surfaces can be touched to pull up a registry, allowing searches for gridlinked vehicle icons by Vehicle Identification Number (VIN), license plate number, or other identifying features. Traffic data is collected, processed, and disseminated in this host as well. | |||
====IC Behavior==== | ====IC Behavior==== | ||
Patrol will be running at all times. If the host is alerted, it will deploy the highest IC in the load order (see IC Tray, leftmost is highest priority). IC follow normal behavior patterns. | Patrol and Bloodhound will be running at all times. If the host is alerted, it will deploy the highest IC in the load order (see IC Tray, leftmost is highest priority); this occurs at the ends of combat turns after the alert goes off due to the processing lag caused by disabling direct connections. IC follow normal behavior patterns. | ||
====Devices==== | ====Devices==== | ||
All devices slaved to this host are protected by the host's attributes due to the industry host protocols. Slaved devices include traffic lights, cameras, data-collecting vehicles and drones, and any other devices used to monitor and/or regulate the flow of traffic. | |||
The vast majority of vehicles on the road are not slaved to GridGuide, but they are usually triple-marked by it so that GridGuide can issue commands to autopilots when necessary. All vehicles with a gridlink will be accessible through this host as a result of their being connected to the host via induction cables in the road, even if their wireless function is disabled; the only vehicles that will not be accessible through this host are vehicles that have their electronics completely turned off, vehicles that lack a gridlink, and vehicles not on the road. Data on registered but inactive vehicles can still be found this way. Vehicles with a Gridlink Override are not marked by this host, and they will be difficult to find through the host's lookup due to the override regularly changing their identifiers. Game masters should set the Matrix Search threshold accordingly. Note that because these vehicles are not slaved to GridGuide, they are not protected by the host's attributes. However, direct connections are not permitted in an industry host, so vehicles may still be protected by a network master's attributes, such as a rigger's RCC or an average person's commlink. | |||
====Spiders==== | ====Spiders==== | ||
Regulations require at least one decker to be patrolling this host at all times, a duty that's usually pushed off on the aforementioned MCT subsidiary deckers due to the host being constantly attacked by script kiddies who are immediately stopped by its defenses before chickening out. If a real threat shows up, the spider(s) will call for backup from a more experienced Mitsuhama corp decker, who is more than willing to melt a few brains to protect the flow of traffic and company assets. | |||
==Physical Integration== | ==Physical Integration== | ||
Many, many devices all across the Seattle 'Plex are slaved to this host, and many more are constantly connected to it. Getting a backdoor into Traffic Control is as easy as popping a panel on a traffic light open and clamping a data tap to the exposed wires. Because it's so easy to infiltrate Traffic Control, it runs industry host protocols, meaning you still have to contend with its firewall and intrusion countermeasures if you want to hack anything remotely. It's a tough enough host that it takes a serious hacker to make any real progress inside, and the threat of Mitsuhama deckers turning your brain to mush is very real. In short, its security against physical access is almost nonexistent, but its cybersecurity is formidable. | |||
Most people don't interact with GridGuide in that fashion, though. The typical use case is that a gridlinked car invites three marks to Traffic Control every time it starts up, and it stays connected via a series of induction cables in the roads that simultaneously power it. GridGuide then sends navigation data to the car's autopilot, which follows its instructions. In the event of an emergency, the host will take the Control Device action on the car with its three-mark authorization, such as to stop it short of a collision it knows is about to occur due to traffic conditions the autopilot can't see yet. Drivers are free to switch to manual control, which overrides the autopilot, but GridGuide always has the power to override manual control with remote control if necessary. | |||
Needless to say, this is a liability to shadowrunners and other criminal elements. As a result, gridlink overrides are a common upgrade to criminal vehicles. Overrides allow a vehicle to use GridGuide without granting marks to Traffic Control, preventing it from using Control Device. They also regularly switch the vehicle's identifiers to confuse the system so this illegal activity is not noticed and becomes much harder to track down even when looking for it intentionally. | |||
==Foundation== | ==Foundation== | ||
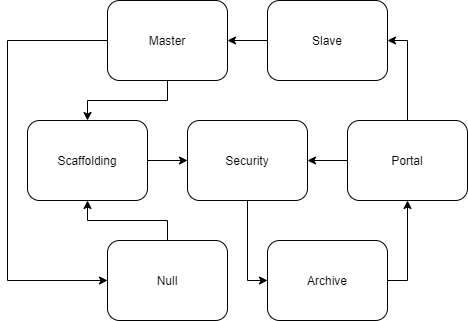
This host's foundation is of tremendous importance, as the Slave node allows any user to apply marks that persist despite reboots, | This host's foundation is of tremendous importance, as the Slave node allows any user to apply marks that persist despite reboots, which is very important for a major city's traffic control system. The archive contains traffic history, old operational documents, and old user data. The foundation's portal is checked weekly for anchors during routine maintenance to protect against sabotage. Because of the lives and money involved in this host's operation, intrusions will not be taken lightly if they are detected. | ||
[[File: | [[File:Gridguide foundation.png]] | ||
[[Category:Hosts]] | [[Category:Hosts]] | ||
Latest revision as of 05:32, 14 April 2020
Description
GridGuide is a city's traffic control system, managed by a central host that sends routing data to vehicle autopilots and can track or control them in the event of an emergency. Contrary to the snazzy name, GridGuide is not a corporation, but a service provided by a corporate contractor; Seattle's GridGuide service is provided by Mitsuhama Computer Technologies. Because devices slaved to this host are ubiquitous in the Seattle Metroplex and easily accessed by hand, it's not hard to hack in. As a result, GridGuide hosts typically operate under Equipment Management Transfer Protocol (EMTP), more commonly known as an "industry host." See the next section for more details.
Scaffolding
The GridGuide host icon looks like a wheel with the Mitsuhama diamond at its center. When approached, it plays a jingle and displays the GridGuide logo as the wheel spins.
Customer Service
| Type | Rating | Attack | Sleaze | Data Processing | Firewall | IC Tray |
|---|---|---|---|---|---|---|
| Destination | 7 | 6 | 6 | 10 | 12 | Patrol, Bloodhound, Tar Baby, Track, Killer, Blaster, Shocker |
Inside, users will find themselves in a sleek, polished corporate reception area. Virtual customer service representatives are always ready to help Seattle's vehicle owners register their cars with GridGuide. There is also a live traffic report feed that can be accessed from here, with the option to download the GridGuide traffic app for updates on the go. Because this is a destination node, one mark is granted freely to anyone who approaches. Silent-running is disabled inside.
IC Behavior
Patrol and Bloodhound will be running at all times, with others kept in reserve. In emergency response mode, the host will spawn the highest priority IC in its IC Tray (see table). As a destination host, it will spawn each IC type per attacking persona at the start of each combat turn, though IC will not interact with any persona other than the one to which they are assigned.
IC will not attack unless a hacker succeeds in an Attack action or fails a Sleaze action. If a hacker does not fight the IC or attempt any further illegal activity, the host will not enter alert, and the IC will stand down. Continued attacks will cause the host to enter emergency response mode; for each attack after the first a host suffers in a combat turn, its Firewall increases by 1 for 2 combat turns. If a hacker's attacks persist longer than 1 combat turn or the host gains 2 marks on them, a spider will be alerted.
Personas with only 1 mark are not subject to Patrol IC scanning.
Devices
This host does not have any slaved devices.
Spiders
There are no spiders on active patrol in this host, but if a spider is alerted, one will appear within a combat turn or two. The first spiders called in will be new acquisitions, deckers brought into the corporation via one of the numerous subsidiaries MCT has purchased in recent years, and so they will lack the experience and firepower of a Zero-Zone veteran. However, if you continue to cause trouble for long enough, a more veteran decker may be called in from corporate security duty for a bit, and they will immediately escalate to lethal force, having no sympathy for you.
Traffic Control
| Type | Rating | Attack | Sleaze | Data Processing | Firewall | IC Tray |
|---|---|---|---|---|---|---|
| Industry | 7 | 9 | 8 | 7 | 10 | Patrol, Bloodhound, Blaster, Tar Baby, Track, Marker, Sparky |
There is an employees-only area that can be accessed through a door marked "TRAFFIC CONTROL." Users who enter are transported into a vast, digital facsimile of Seattle represented as a series of neon-colored wireframe vehicles, traffic devices, roads, and buildings against a black background. Personas are free to fly above the city at blistering speeds, zipping from location to location in an instant. Solid surfaces can be touched to pull up a registry, allowing searches for gridlinked vehicle icons by Vehicle Identification Number (VIN), license plate number, or other identifying features. Traffic data is collected, processed, and disseminated in this host as well.
IC Behavior
Patrol and Bloodhound will be running at all times. If the host is alerted, it will deploy the highest IC in the load order (see IC Tray, leftmost is highest priority); this occurs at the ends of combat turns after the alert goes off due to the processing lag caused by disabling direct connections. IC follow normal behavior patterns.
Devices
All devices slaved to this host are protected by the host's attributes due to the industry host protocols. Slaved devices include traffic lights, cameras, data-collecting vehicles and drones, and any other devices used to monitor and/or regulate the flow of traffic.
The vast majority of vehicles on the road are not slaved to GridGuide, but they are usually triple-marked by it so that GridGuide can issue commands to autopilots when necessary. All vehicles with a gridlink will be accessible through this host as a result of their being connected to the host via induction cables in the road, even if their wireless function is disabled; the only vehicles that will not be accessible through this host are vehicles that have their electronics completely turned off, vehicles that lack a gridlink, and vehicles not on the road. Data on registered but inactive vehicles can still be found this way. Vehicles with a Gridlink Override are not marked by this host, and they will be difficult to find through the host's lookup due to the override regularly changing their identifiers. Game masters should set the Matrix Search threshold accordingly. Note that because these vehicles are not slaved to GridGuide, they are not protected by the host's attributes. However, direct connections are not permitted in an industry host, so vehicles may still be protected by a network master's attributes, such as a rigger's RCC or an average person's commlink.
Spiders
Regulations require at least one decker to be patrolling this host at all times, a duty that's usually pushed off on the aforementioned MCT subsidiary deckers due to the host being constantly attacked by script kiddies who are immediately stopped by its defenses before chickening out. If a real threat shows up, the spider(s) will call for backup from a more experienced Mitsuhama corp decker, who is more than willing to melt a few brains to protect the flow of traffic and company assets.
Physical Integration
Many, many devices all across the Seattle 'Plex are slaved to this host, and many more are constantly connected to it. Getting a backdoor into Traffic Control is as easy as popping a panel on a traffic light open and clamping a data tap to the exposed wires. Because it's so easy to infiltrate Traffic Control, it runs industry host protocols, meaning you still have to contend with its firewall and intrusion countermeasures if you want to hack anything remotely. It's a tough enough host that it takes a serious hacker to make any real progress inside, and the threat of Mitsuhama deckers turning your brain to mush is very real. In short, its security against physical access is almost nonexistent, but its cybersecurity is formidable.
Most people don't interact with GridGuide in that fashion, though. The typical use case is that a gridlinked car invites three marks to Traffic Control every time it starts up, and it stays connected via a series of induction cables in the roads that simultaneously power it. GridGuide then sends navigation data to the car's autopilot, which follows its instructions. In the event of an emergency, the host will take the Control Device action on the car with its three-mark authorization, such as to stop it short of a collision it knows is about to occur due to traffic conditions the autopilot can't see yet. Drivers are free to switch to manual control, which overrides the autopilot, but GridGuide always has the power to override manual control with remote control if necessary.
Needless to say, this is a liability to shadowrunners and other criminal elements. As a result, gridlink overrides are a common upgrade to criminal vehicles. Overrides allow a vehicle to use GridGuide without granting marks to Traffic Control, preventing it from using Control Device. They also regularly switch the vehicle's identifiers to confuse the system so this illegal activity is not noticed and becomes much harder to track down even when looking for it intentionally.
Foundation
This host's foundation is of tremendous importance, as the Slave node allows any user to apply marks that persist despite reboots, which is very important for a major city's traffic control system. The archive contains traffic history, old operational documents, and old user data. The foundation's portal is checked weekly for anchors during routine maintenance to protect against sabotage. Because of the lives and money involved in this host's operation, intrusions will not be taken lightly if they are detected.