Knight-Errant Seattle Police Host

Description
This is the host used by Knight-Errant's police force for the Seattle metroplex. It consists of three parts representing different areas in a police station: Reception, Administration, and Dispatch.
Scaffolding
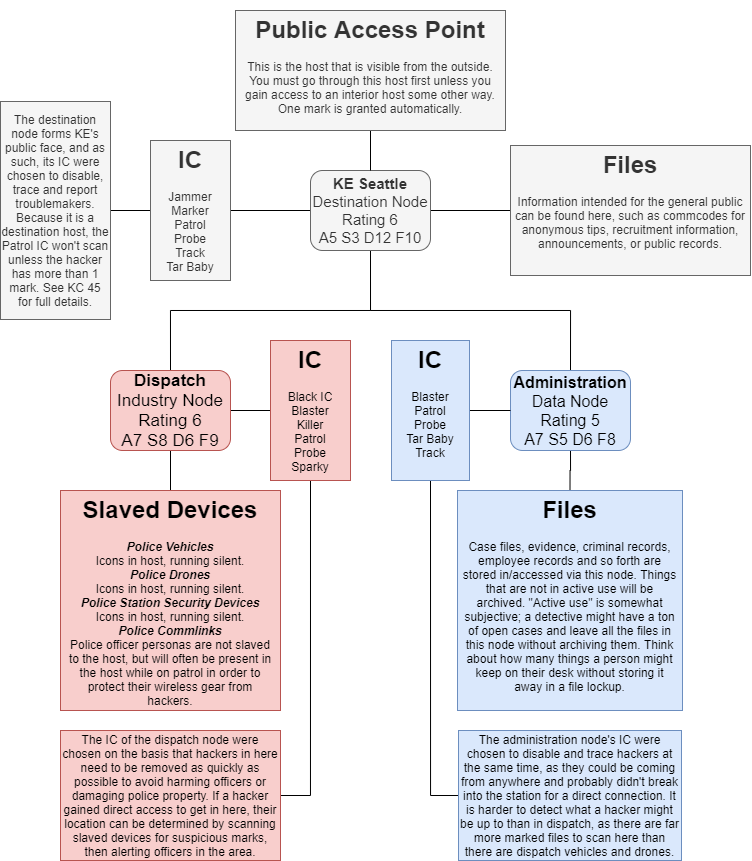
The Knight-Errant police host has a KE police badge as its icon. It always faces you no matter which direction you approach it from. Entering will place you in Reception; a mark will be invited automatically, making it publicly accessible.
Reception
| Type | Rating | Attack | Sleaze | Data Processing | Firewall | IC Tray |
|---|---|---|---|---|---|---|
| Destination | 6 | 5 | 3 | 12 | 10 | Patrol, Probe, Track, Tar Baby, Jammer, Marker |
This is the public face of Knight-Errant's Seattle police force. It looks like a police station, with notice boards, help desks, and contact information for anonymous tips, records requests, departments, and anything else one might expect to find on a police department's website for the public to see. From here, two doors lead to the nested hosts Administration and Dispatch. These are staff-only areas.
IC Behavior
Patrol is deployed at all times, but the others are kept in reserve. The host will spawn the IC highest up in the load order (see IC Tray) that is not currently deployed. IC were chosen with the goal of tracing an offending hacker without causing harm to any script kiddie who might access the host and try something stupid.
As a destination host, the restriction on spawning 1 IC at the beginning of each combat turn is lifted, instead spawning 1 IC per attacking persona at the beginning of each combat turn. IC will not attack unless a hacker succeeds in an Attack action or fails a Sleaze action. If a hacker does not fight the IC or attempt any further illegal activity, the host will not enter alert, and the IC will stand down. Continued attacks will cause the host to enter emergency response mode; for each attack after the first a host suffers in a combat turn, its Firewall increases by 1 for 2 combat turns. If a user's attacks persist longer than 1 combat turn, a spider will be alerted.
Personas with only 1 mark are not subject to Patrol IC scanning.
Devices
There are no devices slaved to Reception.
Spiders
Reception is not normally patrolled by a spider, though if an alert goes out, the spider from Administration will enter Reception to deal with the situation.
Administration
| Type | Rating | Attack | Sleaze | Data Processing | Firewall | IC Tray |
|---|---|---|---|---|---|---|
| Data | 5 | 7 | 5 | 6 | 8 | Patrol, Blaster, Probe, Track, Tar Baby |
The administration node looks like a series of offices and rooms full of filing cabinets. This is accurate, as it is a file repository used by police officers and detectives to manage their active cases. Think about what files you might find looking at an officer's desk, the evidence room, or in any filing cabinets in the offices of police HQ. You're likely to find such things here. Case files, evidence descriptions, criminal records - anything in active use. Closed cases and files not accessed in a long time will be stored in the host's archive, meaning they have to be retrieved by a spider or the file's owner, or a hacker will have to look for them in the host's foundation.
IC Behavior
Patrol is deployed at all times. The host will spawn the IC highest up in the load order (see IC Tray) that is not currently deployed. IC were selected with the goal of immobilizing, marking, and tracing the offending hacker for physical arrest. IC follow standard deployment and behavior rules.
Devices
There are no devices slaved to Administration.
Spiders
An on-duty spider resides in Administration to call up archived files and handle evidence for police officers. Expect them to be fairly well trained and equipped, likely with a cyberdeck of rating 3. They will be exceedingly bored, however.
Dispatch
| Type | Rating | Attack | Sleaze | Data Processing | Firewall | IC Tray |
|---|---|---|---|---|---|---|
| Industry | 6 | 7 | 8 | 6 | 9 | Patrol, Killer, Sparky, Blaster, Black IC, Probe |
The dispatch node resembles a war room, in some respects. A big display of the Seattle metroplex contains icons for cars and drones, and operators sit around it coordinating emergency calls and police vehicle/drone response. Files here will see heavy, constant use, as they contain recent communications records before being sent to administration.
IC Behavior
Patrol is deployed at all times. The host will spawn the IC highest up in the load order (see IC Tray) that is not currently deployed. IC were selected with the goal of eliminating any threats in Dispatch as soon as possible to protect police personnel and materiel. They follow standard IC rules with the exception they are deployed at the ends of combat turns instead of the beginnings, due to the processing lag required to manage all the devices with network security protocols.
Devices
This node protects nearly all Knight-Errant police devices in Seattle. All police vehicles and drones are slaved to this host, as are security devices in in the physical K-E police HQ building. These devices run silent, so anyone looking to hack them will need to have some idea what they're looking for first. High-priority vehicles and drones will be slaved to an RCC that is slaved to the host in order to allow a rigger-spider to manage them. Because Dispatch is an industry host, hackers inside do not have a direct connection to all slaved devices. Be very careful.
Spiders
There is one on-duty decker inside Dispatch at all times, coordinating with the Administration decker and ensuring all the expensive equipment inside remains functional. There is also a rigger-spider on duty to oversee high-priority operations such as SWAT teams. The spiders of Dispatch are better trained and equipped than those of Administration, and they are ruthless. Expect device ratings of 4 and better skillsets.
Physical Integration
All devices in the host are slaved to the Dispatch node, meaning they are not easily accessed from the matrix. They are not usually easy to access physically, either.
Security devices in the police station will be placed outside of reach, such as cameras being on the ceiling behind glass cages. Locks will not be slaved to the host due to how easily they can be accessed. If someone can access a lock to hack it, it should be about as secure as the door's physical integrity, which is to say the average person can't deal with it, but a shadowrunner could easy smash it. Accordingly, it won't provide them a backdoor to all other devices.
Police vehicles can be found all across the sprawl, but getting a direct connection to them requires you to get inside the car, usually. The universal connector port to access the vehicle is always on the dashboard, and the data cables one could clip a tap onto are under the vehicle's hood, running to the back above panels below. In short, they're normally only found in areas a mechanic or police officer would have access to.
Police drones are even harder to get physical access to in a way a hacker would want, as disabling or jamming them will cause them to lose connection to Dispatch and thus the mark one could gain on it. If they are somehow accessed physically while online, the hacker runs the risk of alerting Dispatch before they even enter it, as the drone will almost certainly send an emergency alert.
Foundation
The foundation of the KE Seattle Police host is unanchored and therefore random. The Archive and Slave nodes are of high importance due to the files and devices contained therein. Note that all nested hosts share the same foundation, so Reception, Administration, and Dispatch can all be affected from within.